Bob.Vmem
we are checking for a suspicious file in Bob.vmem dump file.
1. First we have to check the integrity of a dump
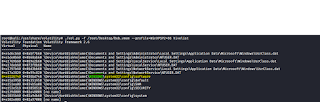
In this we are using imageinfo command. Then it gives as a profile the integrity is good
Command used:
./vol.py -f /root/Desktop/Bob.vmem imageinfo
In above image we get service packs , profile names ,date and time
2. PSlist: Lists out all the process which was running when the image was taken.
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 pslist
 |
| Add caption |
3. PSScan: it mostly used for malware analysis and rootkit scanning ,Lists out all the inactive or hidden or unlinked processes which was either created by rootkit or malware
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 psscan
4. PSXView: Identify the actual hidden processes. As we can see, There are two columns for commands pslist and psscan . if any process has false in psscan then we consider it as a hidden process
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 psscan
In above image I found hidden PIDS and suspected PID : 644 , 4 , 548 , 612 , 452,888,1752
5. Command Scan: It lists out all the commands being typed by users , backdoors and malwares locally or remotely . We got changing ip address commands
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 cmdscan
In above image we didn’t get any commands
6. Socket Scan : It lists out all the connections(TCP/UDP), been made by the local machines.
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 sockscan
In above image we got the tcp/udp connections
7. Connections: It displays all the active connections which were present at the time the image was taken as we can see from the image right now we don’t have any active connections
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 Connections
8. Connscan : Plugin displays all the closed connections, or connection which was closed while image was taken . It has made the connections to the remote ip addresses , and it also displaying the process idientifier also for the same.
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 Connscan
9. Hashdump: we can dump the user accounts passwords for windows based images .
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 hashdump
10. Dumping Suspected Process:
Command used:
./vol.py -f /root/Downloads/CPFA/CPFA.vmem --profile=WinXPSP2x86 memdump -p processid -D /root/Desktop/
In above image we download the suspected process ids using above command
In above image I suspected these files so I dumped all the files
11. Virus Total:
It is a website scans a dump file for finding a suspicious files.
In above image is the home page of the website and we are choose the dump file and upload it then we get result shown in the below image.
I run all the suspected dump files and I got 3 suspicious files PIDS are 548 , 612 , 644,1752 , 888.
548, 612 have two engines detected and it shown in below image.
But for 644,1752 PID It detects 3 engines.It shown in below image.
I have to make sure which PID has been suspected . So I do further steps to determine the how attack happened.
12. Hivelist:it list out all the registry entries present in the memory image/RAM dump along with all the physical and virtual addresses.
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 hivelist
In above image I found a software registry . so I just try to get in to the path using virtual address of that registry
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 printkey -o 0xe1526748
In above image we got some subkeys and I decided to go to the Microsoft key. In above image we didn’t get any values
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 printkey -o 0xe1526748 -K "Microsoft"
In above image I got so many subkeys and I decided to go Windows NT Subkey. In above image we didn’t get any values.
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 printkey -o 0xe1526748 -K "Microsoft\Windows NT"
In above I didn’t get any values and I got only one subkey CurrentVersion . So I Decided to go to the that subkey.
Command used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 printkey -o 0xe1526748 -K "Microsoft\Windows NT\CurrentVersion"
In above image I got the values. That means some one modify the data in the system in this I got name:Bob and installed path in c drive
In above I got so many subkeys and I find a winlogin subkey which was I suspected in the virus total PID:644 . so I decided to go and check that Winlogin
Command Used:
./vol.py -f /root/Desktop/Bob.vmem --profile = WinXPSP2x86 printkey -o 0xe1526748 -K "Microsoft\WindowsNT\CurrentVersion\Winlogon"
In above I got some details and those details listed in below:
1. Shell :
Explorer.exe: It is the default shell for windows. It IS NOT vital for explorer to be running to use Windows. And it is possible for explorer to chew up 98% percent CPU, if it starts behaving badly. If you open the task manager (CTRL+ALT+DEL), you can kill explorer, and use the task manager to start and stop programs.
2. Userint :
A. Userint.exe:It is the file responsible for executing logon scripts, reestablishing network connections and then starting Explorer.exe, and is a safe file for your PC. Winlogon is an essential component of the Windows series of operating systems that handles the secure loading of a user profile at the time of login.
B. Sdra64.exe:It is an executable file created by Trojan.Zbot, a malicious computer program that steals sensitive information from a computer.
So attacker upload a pdf file in internet .Victim download that PDF file , when the file downloaded malicious(Sdra64.exe) started working and corrupt entire system . and attacker used userint.exe application to create a alternate login and captured the data what he wants from victims machine
In above information are saying that system has been compromised by an a application trojan which was installed by an a attacker while user using Administrator account. Suspected Process id is “644, 1752 , 888”























Comments
Post a Comment