Hackademic challenge 1 - 5
Hackademic Ch 1 - 5
The OWASP Hackademic Challenges implement realistic scenarios with known vulnerabilities in a safe, controllable environment. Users can attempt to discover and exploit these vulnerabilities in order to learn important concepts of information security through the attacker's perspective.Currently, there are 10 web application security scenarios available.
Link: http://hackademic.teilar.gr/index.html
Challenge : 1
What to find:
Our agents (hackers) informed us that there reasonable suspicion that the site of this Logistics Company is a blind for a human organs' smuggling organisation.
This organisation attracts its victims through advertisments for jobs with very high salaries. They choose those ones who do not have many relatives, they assasinate them and then sell their organs to very rich clients, at very high prices.
These employees are registered in the secret files of the company as "special clients"!
One of our agents has been hired as by the particular company. Unfortunately, since 01/01/2007 he has gone missing.
We know that our agent is alive, but we cannot contact him. Last time he communicated with us, he mentioned that we could contact him at the e-mail address the company has supplied him with, should there a problem arise.
The problem is that when we last talked to him, he had not a company e-mail address yet, but he told us that his e-mail can be found through the company's site.
The only thing we remember is that he was hired on Friday the 13th!
You have to find his e-mail address and send it to us by using the central communication panel of the company's site.
Sol :
First we enter to the logistics company website
In above image we have to login the website . so I decided to check source code of web page.
In above image I found a white:rabbit . Then I tried to login using these details.
In above image I entered user as a white and password as a rabbit.
Then submitted I logged in to the account .
In above image we have some directories on left
Then I selected last one “Mailbox Special Clients Mailbox”.
In above image highlighter one is a image .
So I copied the image path and paste it on new tab .
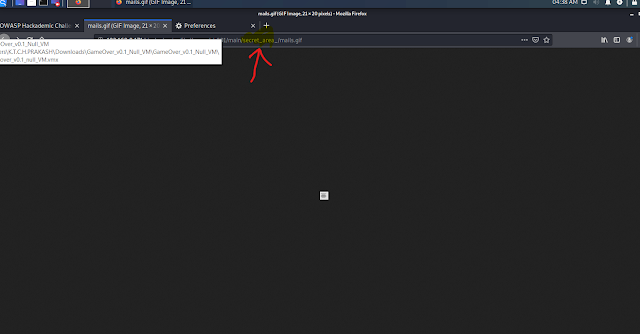
Copied Image path: http://192.168.0.171/Hackademic_Challenges/ch001/main/secret_area_/mails.gif
Then I got this output .
In url I remove the mails.gif and then entered.
Modified Url: http://192.168.0.171/Hackademic_Challenges/ch001/main/secret_area_
In above image I got mails.gif and mails.list.
Mails.gif means a picture we already seen .
Lets go the mails.list.
In Question they mentioned agent send a message “ Friday 13th” .
So I assumed that agent mail id is Friday13@JasonLives.com .
So I get back and go the send e-mail option .
In above image I entered the agents mail id and I didn’t filled ay column and sent.
Then we got a Congratulations message .
Challenge 2:
What to do:
Your Country needs your help for finding the password of an enemy site that contains useful information, which if is not acquired on time, peace in our area will be at stake.
You must therefore succeed in finding the password of this military SITE.
Sol:
First we enter to the website:
Then I go to the page source and I copied the code.
Then I go to the “jsbin.com” and paste the code.
Then I go through the code to find vulnerability .
Then I found that in code they give wrong but they didn’t give “document.write(wrong).
In above image I modify the code and entered.
Then I got a message.
I copied that message and pasted in the password text field.
Then I entered .
Then I got a congratulations message .
Challenge 3:
What to do:
XSS permits a malevolent user to inject his own code in vulnerable web pages. According to the OWASP 2010 Top 10 Application Security Risks, XSS attacks rank 2nd in the "most dangerous" list.
Your objective is to make an alert box appear HERE bearing the message: "XSS!".
Sol:
First we need to enter the web site .
Then we have to XSS payload : <script>alert(“XSS!”);</script>
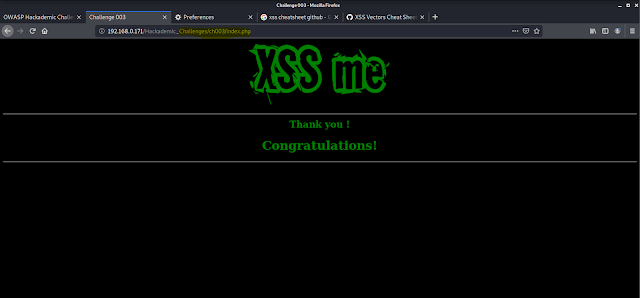
Then we got the pop-up message(XSS!) .
After click ok we got the congratulations message .
Challenge 5:
What to do:
You need to get access to the contents of this SITE. In order to achieve this, however, you must buy the "p0wnBrowser" web browser. Since it is too expensive, you will have to "fool" the system in some way, so that it let you read the site's contents.
Sol:
First we have to enter the web site.
In above image I copied p0wnBrowser .
Then we can use burpsuite or tampered data extensions which is available in firefox store.
In this I used tampered data extension.
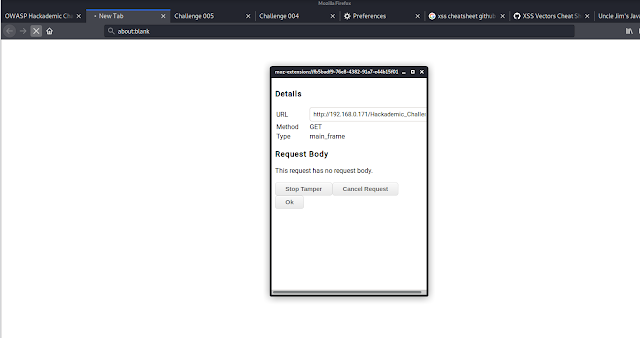
Then I start the tampered data extension .
Then I refresh the web site and data has been captured.
Then I got the details of web site like user-agent , host etc.
So I decide to replace the user agent with p0wnBrowser and then entered .
Then I got a congratulations message.


























Comments
Post a Comment