Hackademic Challenge 6 -10
Hackademic Ch 6 - 10
Link: http://hackademic.teilar.gr/index.html
Challenge 6:
What to do :
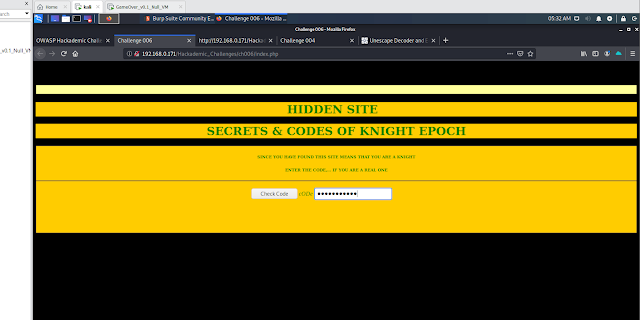
In this assignment you must prove your... knightly skills! Real knights have not disappeared.
They still exist, keeping their secrets well hidden.
Your mission is to infiltrate their SITE. There is a small problem, however... We don't know the password!
Perhaps you could find it?
Sol:
First we have to enter the website.
Then I go the source code and I found that are encoded so I have copied encoded part .
And pasted in the online Unescape encoded and decoded tool.
Then click the decode button .
We got decoded output and copied and pasted in the code writer. Then I go through the code
Later I found getpassinfo column in 128th line of code. And it is highlighter in the above image.
Then I copied the password and enter in tthe website.
Then click the check code.
Then I got the congratulations message.
Challenge 7:
What to do :
A good friend of mine studies at Acme University, in the Computer Science and Telecomms Department. Unfortunately, her grades are not that good. You are now thinking "This is big news!"... Hmmm, maybe not. What is big news, however, is this: The network administrator asked for 3,000 euros to change her marks into A's. This is obviously a case of administrative authority abuse. Hence... a good chance for D-phase and public exposure...
I need to get into the site as admin and upload an index.htm file in the web-root directory, that will present all required evidence for the University's latest "re-marking" practices!
I only need you to find the admin password for me...
Sol:
First we enter to the website .
We have to get login details .
So I copied the image path of ACME University and pasted in the new tab
Image url: http://192.168.0.171/Hackademic_Challenges/ch007/index_files/logo.ping
After that I removed logo.ping in url to see any thing is available .
Modified URL : http://192.168.0.171/Hackademic_Challenges/ch007/index_files/
In above image I got three modules which are background.jpg , lastlogin.txt , loh0.ping .
I selected lastlogin.txt file to check the login details.
In above image I got the name irene. He is the last logged person .
Using this account I have to get the access of admin.
So I enter Irene in the website .
Then I logged in to the Irene account as a user . but I didn’t get admin privilege .
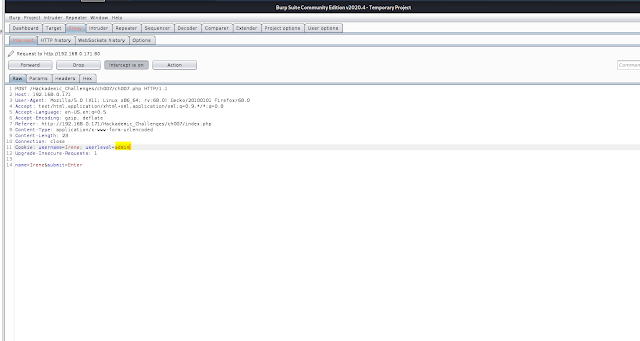
In above image I capture the data while logging .
In that data it shows user-level as a user.
So I decided to change that in to the admin . to get the admin privilege .
In above I modified user-level : user to admin
And then click on the forward I got another data.
In above I modified user-level : user to admin
And then click on the forward I got another data.
In this also user -level still shows user .
Again I do modify the user to admin.
Then click on the forward . later I didn’t capture any data. So I went to the website
In above image I got congratulations message.
Chapter 8:
What to do :
You have managed, after several tries, to install a backdoor shell (Locus7Shell) to trytohack.gr
The problem is that, in order to execute the majority of the commands (on the machine running the backdoor) you must have super-user rights (root).
Your aim is to obtain root rights.
Sol:
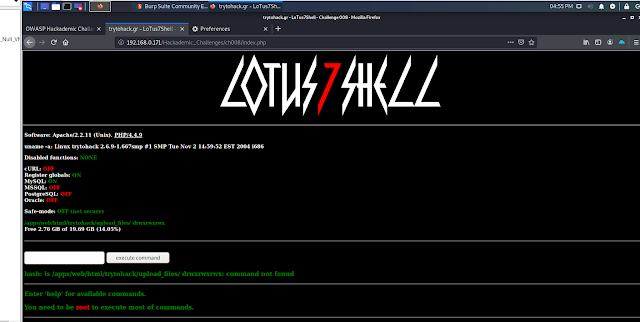
First we go to the website.
In above image I got a web shell in this we run a linux commands to gain root access .
So first I decided to see which commands are worked in the web shell .
Command used: help
Then I got a list of commands used in this web shell.
Then I decided to intercept the data using burp suite .
Then I give a list command.
Command used:ls
I capture the data in burpsuite and select intercept option before click on the forwarding.
After that I clicked on the forward.
In above image I got the intercept data as a source code of website . In that I found a text file in the name of b64.txt .
So I go to the website and I removed index.php and added b64.txt .
Then I got the base 64 encoded data .
So I use the base 64 decoder online tool to find the data .
In above image I got the decoded data.
In that we have user name and password using this we logged in to the super user account .
Command used : su
In linux “su” is used for logged in to the root account .
Then I got another two columns in webshell .
In that I enter the username: root and password : g0tr00t
Then I enter to the root account .
In above image I got a congratulations message .
Chapter 10:
What to do:
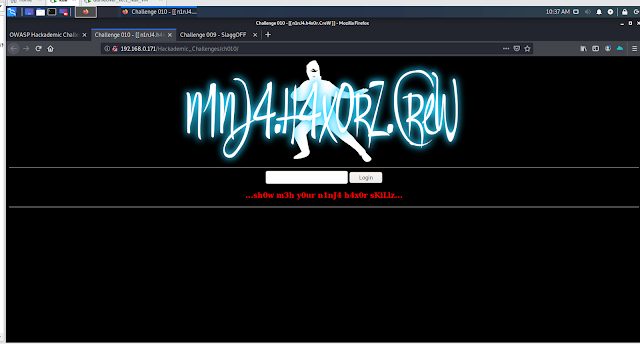
Would you like to become an active hacker ?
How about becoming a member of the world's largest hacker group:
The n1nJ4.n4x0rZ.CreW!
Before you can join though, you 'll have to prove yourself worthy by passing the test that can be found at: http://n1nj4h4x0rzcr3w.com
If you succeed in completing the challenge, you will get a serial number, which you will use for obtaining the password that will enable you to join the group.
Your objective is to bypass the authentication mechanism, find the serial number and be supplied with your own username and password from the admin team of the site.
Sol:
First we enter the website .
I go to the page source code in that I found some vulnerability which is highlighted in the below image .
So I decided to intercept the data using burp suite .
In above image I got a data so I decided to modify false to true .
Because if we using false we wont login which ever credentials used. So I decided to use true , using this true we logging without entering any data.
Then I clicked on the forward . later I didn’t capture any data on burpsuite so I go to the website.
In website there is a pop- up message . in that message we have base-64 encoded message.
It shown in below image.
Then I copied the encoded message .
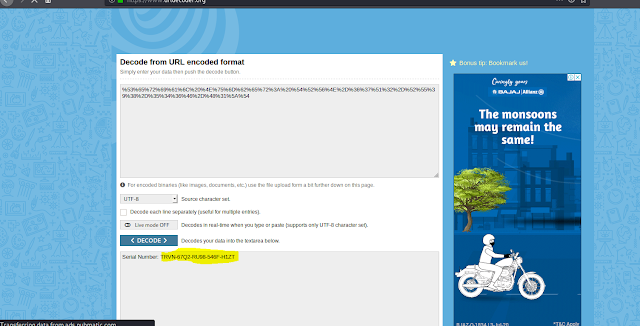
Then I go to the online base 64 decoder tool to decode the message . then I pasted the encoded message in the decoded website.
In above image I decoded the message and I got the serial number .
Then I get back to the pop-up message and click on ok.
Then it takes me to another path.
In above image I got the To , From , Subject , Serial Number .
So I enter the serial number which I got in the decoded message and click on send button .
Then I got the congratulations message .


































Comments
Post a Comment